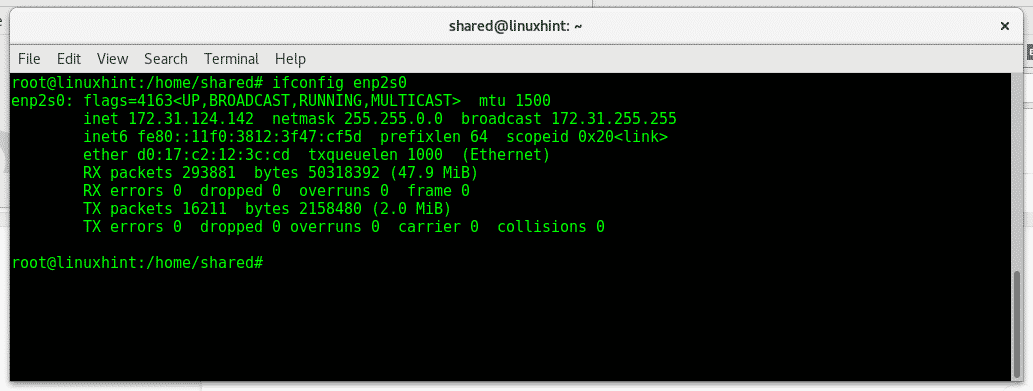
So you have bought your Raspberry Pi but you don’t have a screen. How can you connect to it. Thankfully the Raspberry Pi has SSH enabled by default, enabling you to connect using SSH. An SSH connection will give you command line access to the Pi and you can use the SSH client on another Linux host or OSX system. Failing that you can install PuTTY in Windows. You know what, I need to know the IP Address of the Raspberry Pi and I don’t have it. Adding a screen to the Pi is a solution but it is beginning to feel a little like the song, there is a hole in my bucket. We are going to discover how we can: “Find My Raspberry Pi using NMAP”.
Keeping Hardware to the Minimum
We will demonstrate how we can connect to the Pi with just and Ethernet cable without the need of adding in a screen, keyboard or mouse. The Pi will have power and an ethernet cable and this is all.
Host scan is used by penetration tester to identify active host in a network by sending. The Windows, Mac, and Linux versions of the program can be downloaded here. For Windows, Nmap comes with a custom installer (nampsetup.exe). Download and run this installer, and it automatically configures Nmap on your system. On Mac, Nmap also comes with a dedicated installer. Run the Nmap-mpkg file to start this installer. MAC Address: 00:1A:4D:58:1A:06 (Giga-byte Technology) Nmap done: 131 IP addresses (2 hosts up) scanned in 6.52 seconds. 3) Specify a scan range of IPs using a wildcard. Nmap 192.168.10. 4) Specify a scan range of IPs using a subnet notation. Nmap 192.168.10.0/24. Scan all ports of an IP range.
Raspberry Pi is SSH Enabled
As we have already mentioned the Secure Shell Server is running by default on the Raspberry Pi, certainly in the Raspbian Distribution. Connecting is simple using the SSH client from another Linux host or Apple OSX system. On Windows based systems there is an SSH client available at no cost called PuTTY. You will need to download and install this. Once a connection has been made then you can work on the command line or install something like XRDP to allow remote desktop connections to the Pi. The difficulty we have to overcome is locating the IP Address of the Pi. This is the network address that we need to connect to.
Use Wired Connection
If you are using the Raspberry Pi 3 it does come with a built-in WiFi connection, however, at least to begin with we will need a wired connection as we have no method of specifying the WiFi network to connect to if we have not added a screen and keyboard. If using the Pi at home it will connect to the network through the ethernet cable to your hub where it will be assigned an IP Address. Great just what we want, but we will not know the address that has been issued. So we still have a problem!
Install NMAP
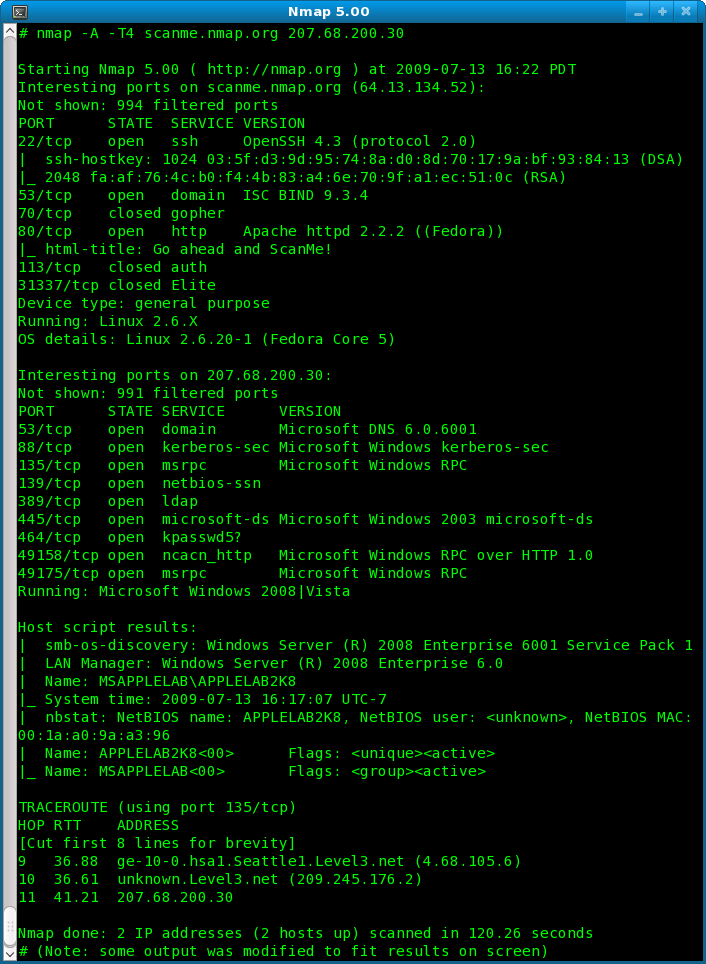
NMAP or the Network Mapper is a tool originally developed in 1997 for Linux. Availability is much better now with versions for OSX, Windows and Unix systems as well as the original Linux platform. NMAP can be used by system administrators in locating threats on their network, but we will see how we can find my raspberry pi using NMAP. Make sure that the host we install NMAP onto is on the same network as the Raspberry Pi need locating. In the video, we are using a CentOS Linux system and we install nmap using the command:
Using a Debian based system like Ubuntu or even Raspbian we would use the apt suite to install nmap:
Using the MAC Address To Identify a Pi
The MAC Address, or Media Access Control Address, of a host, identifies the serial number of the Network Card. This serial number can be traced back to a vendor. For the Raspberry Pi Foundation, the MAC Address will begin with the characters B8:27:EB. Scanning the network with nmap we can return hosts that are up and their MAC Address. Make you are running the command as root or with sudo as the MAC Address is not returned if you run the command as a standard user. I am using the address range 192.168.0.0/24 as that is the network that I have at home. You will need to adjust to match your network.
This should not take too long, perhaps 10 seconds or so. You can always hit the ENTER key to get an update on the progress of the scan. If you have many hosts connected to the network and this may include mobile phones and tablets then we can filter further by piping the result to AWK.
Using AWK to Search the Results
Each record for a running host will be printed in a format similar to the following. Firstly a listing start with Nmap and ends with the MAC Address:
We can see that this relates to an HP system from the returned MAC Address. The databases read by nmap to identify the MAC address prefix is the text file, /usr/share/nmap/nmap-mac-prefixes. The important information to note that the MAC address is display first and is followed on the next line with the IP Address. We really want to display just the IP Address fo those hosts that have a MAC address from Raspberry Pi. We do this with the following command.
Piping the output of nmap to awk we can filter the displayed results. Breaking the awk command down:
/^Nmap/ Search the output for lines beginning with Nmap. This will yield lines similar to:
{ipaddress=$NF} The total number of fields in a record is shown by NF. We assign the last field to a variable IP address. The last field in the output is the IP address if we check the output from the previous command.
/B8:27:EB/ We now search for the MAC address of an RPi in the already filtered output.
{print ipaddress} If we do match on both the Nmap and Mac Address searches we have found a Pi and we print the IP Address which awk previously stored.
If we wanted a simpler awk command that displays the complete matches upi may prefer this syntax.
The video follows.
As always during reconnaissance, scanning is the initial stage for information gathering.
What is Reconnaissance?
Reconnaissance is to collect as much as information about a target network as possible. From a hacker’s perspective, the information gathered is very helpful to make an attack, so to block that type of malicious attempt, generally a penetration tester tries to find the information and to patch the vulnerabilities, if found. This is also called Footprinting. Usually by information gathering, someone can find the below information:
- E-mail Address
- OS details
- Traceroute information/DNS information
- And many more…
So for information gathering, scanning is the first part. For scanning, Nmap is a great tool for discovering Open ports, protocol numbers, OS details, firewall details, etc.
Introduction To Nmap
Nmap (Network Mapper) is an open-source tool that specializes in network exploration and security auditing, originally published by Gordon “Fyodor” Lyon. The official website is (http://nmap.org). Nmap is a free and open source (license) utility for network discovery and security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime.
Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics. It was designed to rapidly scan large networks, but works fine against single hosts. Nmap runs on all major computer operating systems, and official binary packages are available for Linux, Windows, and Mac OS X.
Ethical Hacking Training – Resources (InfoSec)

Installation Of Nmap
Nmap has great support for different environments.
Windows: Install from the official site http://nmap.org For Windows, both GUI and command line options are available. The GUI option for Nmap is Zenmap.
Linux (Ubuntu and Debian): Fire the command in the Linux terminal: apt-get install nmap
In the below image, I have already installed Nmap.
For Red Hat and Fedora based systems: yum install nmap
For Gentoo Linux based systems: emerge nmap
Here, I will show everything in the Linux terminal.
Nmap Scripting Engine
The Nmap Scripting Engine (NSE) is one of Nmap’s most powerful and flexible features. It allows users to write (and share) simple scripts to automate a wide variety of networking tasks. Basically these scripts are written in Lua programming language. Generally Nmap’s script engine does lots of things, some of them are below:
Network discovery
This is Nmap’s bread and butter. Examples include looking up WhoIs data based on the target domain, querying ARIN, RIPE, or APNIC for the target IP to determine ownership, performing identd lookups on open ports, SNMP queries, and listing available NFS/SMB/RPC shares and services.
Vulnerability detection
When a new vulnerability is discovered, you often want to scan your networks quickly to identify vulnerable systems before the bad guys do. While Nmap isn’t a comprehensive vulnerability scanner, NSE is powerful enough to handle even demanding vulnerability checks. Many vulnerability detection scripts are already available, and they plan to distribute more as they are written.
Backdoor detection
Many attackers and some automated worms leave backdoors to enable later reentry. Some of these can be detected by Nmap’s regular expression-based version detection.
Vulnerability exploitation
As a general scripting language, NSE can even be used to exploit vulnerabilities rather than just find them. The capability to add custom exploit scripts may be valuable for some people (particularly penetration testers), though they aren’t planning to turn Nmap into an exploitation framework such as Metasploit.
As you can see below, I have used (-sc) options (or –script), which is a default script scan for the target network. You can see we got ssh, rpcbind, netbios-sn but the ports are either filtered or closed, so we can say that may be there are some firewall which is blocking our request. Later we will discuss how to identify firewalls and try to evade them.
Now I m going to run a ping scan with discovery mode on (script) so that it will try all possible methods for scanning, that way I will get more juicy information.
As you can see in the image, it is trying all possible methods as per script rules. See the next image for more information.
Can you see the interesting ports and protocols? You can see dns-bruteforce found that host contains some blog, cms, sql, log, mail, and many more. So here we can perform SQL injection, the blog may be WordPress, Joomla, etc., so we can attack for a known CMS vulnerability, and obviously the method will be black-box pentesting.
In the upcoming chapter I will describe how to write your own Nmap script engine, and how to exploit them using Nmap.
Basic Scanning Techniques
So here I will show the basic techniques for scanning network/host. But before that, you should know some basic stuff regarding Nmap status after scanning.
Port Status: After scanning, you may see some results with a port status like filtered, open, closed, etc. Let me explain this.
- Open: This indicates that an application is listening for connections on this port.
- Closed: This indicates that the probes were received but there is no application listening on this port.
- Filtered: This indicates that the probes were not received and the state could not be established. It also indicates that the probes are being dropped by some kind of filtering.
- Unfiltered: This indicates that the probes were received but a state could not be established.
- Open/Filtered: This indicates that the port was filtered or open but Nmap couldn’t establish the state.
- Closed/Filtered: This indicates that the port was filtered or closed but Nmap couldn’t establish the state.
Let’s Scan Hosts
Scan A Single Network
Go to your Nmap (either Windows/Linux) and fire the command: nmap 192.168.1.1(or) host name.
Scan Multiple Network/Targets
In Nmap you can even scan multiple targets for host discovery/information gathering.
Command: map host1 host2 host3 etc….It will work for the entire subnet as well as different IP addresses.
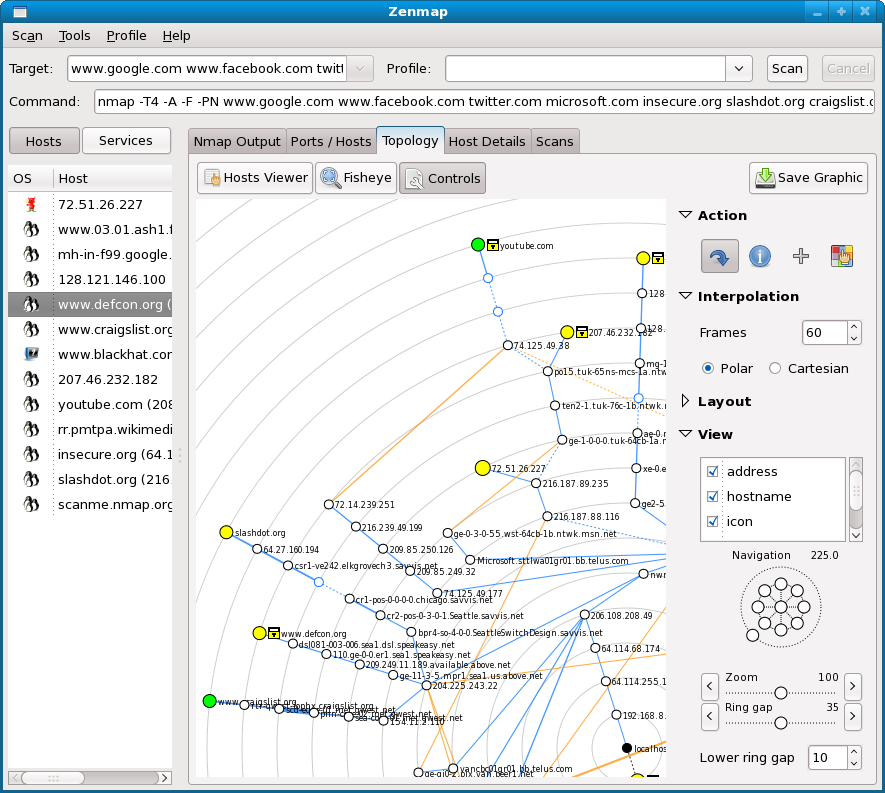
You can also scan multiple website/domain names at a time with the same command. See the below picture. It will convert the domain name to its equivalent IP address and scan the targets.
Scan a Range Of IP address
Command:nmap 192.168.2.1-192.168.2.100
Nmap can also be used to scan an entire subnet using CIDR (Classless Inter-Domain Routing) notation.
Usage syntax: nmap [Network/CIDR]
Ex:nmap 192.168.2.1/24
Scan a list of targets
If you have a large number of systems to scan, you can enter the IP address (or host names) in a text file and use that file as input for Nmap on the command line.
syntax: nmap -iL [list.txt]
Scan Random Targets
The -iR parameter can be used to select random Internet hosts to scan. Nmap will randomly generate the specified number of targets and attempt to scan them.
syntax: nmap -iR [number of host]
It is not a good habit to do a random scan unless you have been given some project.
The –exclude option is used with Nmap to exclude hosts from a scan.
syntax: nmap [targets] –exclude [host(s)]
ex:nmap 192.168.2.1/24 –exclude 192.168.2.10
Aggressive Scan
The aggressive scan selects most commonly used options within Nmap to try to give a simple alternative to writing long strings. It will also work for traceroute, etc.
Command:nmap –A host
Discovery With Nmap
Discovery with Nmap is very interesting and very helpful for penetration testers. During discovery one can learn about services, port numbers, firewall presence, protocol, operating system, etc. We will discuss one by one.
Don’t Ping
The -PN option instructs Nmap to skip the default discovery check and perform a complete port scan on the target. This is useful when scanning hosts that are protected by a firewall that blocks ping probes.
Syntax:nmap –PN Target
By specifying these options, Nmap will discover the open ports without ping, which is the unpingable system.
Ping Only Scan
The -Sp option is responsible for a ping only scan. It will be more useful when you have a group of IP addresses and you don’t know which one is reachable. By specifying a particular target, you can get even more information, like MAC address.
Syntax:nmap –Sp target
TCP Syn Scan
Before we start, we must know the syn packet.
Basically a syn packet is used to initiate the connection between the two hosts.
The TCP SYN ping sends a SYN packet to the target system and listens for a response. This alternative discovery method is useful for systems that are configured to block standard ICMP pings.
The -PS option performs a TCP SYN ping.
Syntax:nmap –PS targets
The default port is port80. You can also specify other ports like –PS22, 23, 25, 443.
TCP Ack Ping Scan
This type of scan will only scan of Acknowledgement(ACK) packet.
The -PA performs a TCP ACK ping on the specified target.
The -PA option causes Nmap to send TCP ACK packets to the specified hosts.
Syntax:nmap –PA target
This method attempts to discover hosts by responding to TCP connections that are nonexistent in an attempt to solicit a response from the target. Like other ping options, it is useful in situations where standard ICMP pings are blocked.
UDP Ping scan
The –PU scan only on udp ping scans on the target. This type of scan sends udp packets to get a response.
Syntax:nmap –PU target
You can also specify the port number for scanning, like –PU 22, 80, 25, etc. In the above picture, the target is my LAN’s IP, which doesn’t have any UDP services.
Sctp init ping
The -PY parameter instructs Nmap to perform an SCTP INIT ping. This option sends an SCTP packet containing a minimal INIT chunk. This discovery method attempts to locate hosts using the Stream Control Transmission Protocol (SCTP). SCTP is typically used on systems for IP based telephony.
Syntax:nmap –PY target
In the picture, though there is no sctp services on the machine, we have to use the –pn option for discovery.
ICMP Echo ping
The -PE option performs an ICMP (Internet Control Message Protocol) echo ping on the specified system.
Syntax:nmap –PE target
This type of discovery works best on local networks where ICMP packets can be transmitted with few restrictions.
Nmap Scan For Mac Address
ICMP Timestamp ping
The -PP option performs an ICMP timestamp ping.
ICMP Address mask ping
The -PM option performs an ICMP address mask ping.
Syntax:nmap –PM target
This unconventional ICMP query (similar to the -PP option) attempts to ping the specified host using alternative ICMP registers. This type of ping can occasionally sneak past a firewall that is configured to block standard echo requests.
Mac Address Cmd
IP Protocol Ping
The -PO option performs an IP protocol ping.
Syntax:nmap –PO protocol target
An IP protocol ping sends packets with the specified protocol to the target. If no protocols are specified, the default protocols 1 (ICMP), 2 (IGMP), and 4 (IP-in-IP) are used.
ARP ping
The –PR option is used to perform an arp ping scan. The -PR option instructs Nmap to perform an ARP (Address Resolution Protocol) ping on the specified target.
SYTAX: nmap –PR target
The -PR option is automatically implied when scanning the local network. This type of discovery is much faster than the other ping methods.
Traceroute
The –traceroute parameter can be use to trace the network path to the specified host.
Syntax: nmap –traceroute target

Force Reverse DNS Resolution
The -R parameter instructs Nmap to always perform a reverse DNS resolution on the target IP address.
Syntax: nmap –R target
The -R option is useful when performing reconnaissance on a block of IP addresses, as Nmap will try to resolve the reverse DNS information of every IP address.
Disable Reverse DNS Resolution
The -n parameter is used to disable reverse DNS lookups.
Syntax:nmap –n target
Reverse DNS can significantly slow an Nmap scan. Using the -n option greatly reduces scanning times – especially when scanning a large number of hosts. This option is useful if you don’t care about the DNS information for the target system and prefer to perform a scan which produces faster results.
Alternative DNS lookup method
The –system-dns option instructs Nmap to use the host system’s DNS resolver instead of its own internal method.
Syntax:nmap –system-dns target
Manually Specify DNS server
The –dns-servers option is used to manually specify DNS servers to be queried when scanning.
Syntax: nmap –dns-servers server1 server2 target
The –dns-servers option allows you to specify one or more alternative servers for Nmap to query. This can be useful for systems that do not have DNS configured or if you want to prevent your scan lookups from appearing in your locally configured DNS server’s log file.
List Scan
The -sL option will display a list and performs a reverse DNS lookup of the specified IP addresses.
Syntax:nmap –sL target
In the next installment, I will discuss how to discover services, host, and banners using different methods, and will also discuss how to find firewalls and how to evade them using NSE by Nmap, and how to write your own Nmap script engine. The most important part of Nmap is knowing how to find vulnerability and try to exploit them. Stay tuned.
Reference
Nmap Ip List
http://nmap.org/
